Business Justification for Secure Content Appliances
Why does an organization need another security device for securing content?
Security professionals are not at a loss for tools and applications to thwart threats to their IT infrastructure. So why do we need to consider yet another kind of application, this time for securing content?
The simple answer is that security tools are tuned for particular problems and no one tool will ever address all security needs. As new threats emerge, so will tools that address those threats. Consider some types of security tools and applications commonly found in enterprise IT environments:
- Network monitoring tools—These programs capture network traffic and allow network administrators to analyze operations on their networks. These are useful for detecting port scans, identifying the source of unusually large volumes of traffic (for example during a Denial of Service—DoS—attack), or probes, such as CGI attacks.
- Firewalls—This ubiquitous security device is a basic tool for controlling the flow of traffic into and out of a network. Firewalls have evolved from being simply a perimeter device to a desktop application that provides protection for individual computers.
- Vulnerability assessment—One of the earliest and best known vulnerability assessment tools, SATAN, garnered mixed responses from security professionals. It provided systems administrators (and hackers) with a single tool to probe computers for a large number of known vulnerabilities, such as unpatched applications. Today, vulnerability assessment tools are considered another essential tool in the security analyst's toolbox.
- Intrusion Prevention Systems (IPS)—These systems began as Intrusion Detection Systems (IDSs) that used sophisticated rules and patterns of network traffic to detect attacks on a network or server. Instead of just detecting attacks, IPS devices can stop them as well by closing down sessions, blocking traffic from specific Internet addresses, and other methods. IPSs can work on either a network or host level.
- Antivirus software—As the name implies, antivirus software identifies and removes malicious code that attaches itself to other programs. Like other security applications, antivirus software has evolved to counter related threats including worms, Trojan horses and blended threats (this type of malware includes multiple malicious programs, such as viruses, worms, keyloggers, file transfer programs, Internet chat clients, and so on).
- Identity management systems—Identity management is the practice of tracking and controlling access to information assets based on a person's—or in some cases, an application's—privileges. Identity management systems combine the features of authentication systems, such as Single Sign-On (SSO) applications, with authorization systems that track a person's roles and privileges.
- Encryption applications—Encryption programs encode data so that only those authorized to see the data may have access to it. This type of application is a basic security technology used in Web protocols, such as SSL; authentication systems; and end-user programs, such as Pretty Good Privacy (PGP). As more and more data is stored on mobile devices and shared storage arrays, such as SANs, encrypting data on disks is becoming more common.
There are other, more specialized tools and applications for security professionals but this list gives a sense of the breadth of security devices already deployed within enterprise environments. Do you really need another security tool thrown into the mix? Couldn't the need be filled by an existing tool or combination of tools?
The answers are, respectively, yes and no. Yes, there is a need for another type of tool to meet threats that are conveyed through content, such as email messages and Web content. The tools mentioned in the previous list are designed and configured to address a narrow range of problems, such as blocking access to ports. With the exception of antivirus software, the tools mentioned do not target the high-level content that moves in and out of a network.
To secure content, you need an application specifically designed for that problem. The characteristics of an appropriate tool include:
- Operates at the application layer of the network—As Figure 1.1 shows, network operations are divided into seven logical layers. Security tools typically function best at one layer; for example, packet sniffers work at the data link and network layers while identity management systems work at the application layer. To effectively analyze the threat embedded in content, the tool must function at the application layer.
- Analyzes all content entering or leaving the network—Email, instant messages, and Web content are the most likely means of brining malware into an enterprise network. Scanning and removing viruses, worms, Trojan horses, and other threats after they reach the server or desktop is one approach; a better method is to prevent it from entering the network at all.
- High-performance analysis—Securing content should not slow email or Web services. Secure content applications should analyze content and allow permissible content to reach its destination with virtually no impact on transmission times.
- Highly accurate analysis—The process for identifying threatening content should have low rates of false positives (categorizing allowed content as not allowed) and false negatives (categorizing non-allowed content as allowed).
- Tamper-proof—The system that is analyzing content should not itself become compromised by malware or attacks.
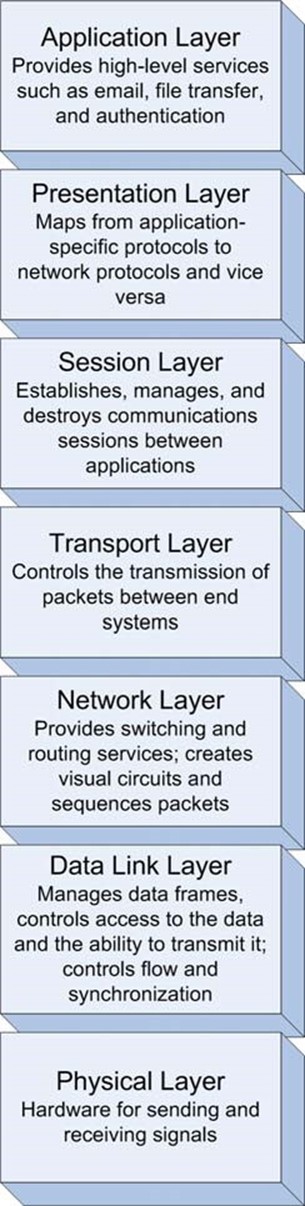
Figure 1.1: The OSI network model includes seven logical layers; security measures must address threats at every layer.
The best method for achieving all these objectives is to deploy a secure content application, service, or appliance.
How does a secure content device complement other security devices?
A secure content device compliments several of the security devices mentioned in question 1.1, including:
- Desktop antivirus
- Firewalls
- Intrusion prevention systems (IPSs)
- Policy administration
No single security device can address all security threats; in addition, some degree of overlap provides supplementary protection to an enterprise's information infrastructure.
Desktop Antivirus
Both secure content devices and desktop antivirus software scan for malware—why use both? Ideally, viruses, worms, Trojan Horses, and other malware would never enter an enterprise network. Secure content devices scan network traffic that is likely to carry malware payloads— especially email, file transfer, and Web-based traffic. Secure content devices can identify and block malware at the perimeter of the network; however, there are other means for malware to enter the organization.
Mobile devices, especially laptops, are not continuously protected by secure content devices. Employees take laptops home to insecure home networks. Sales staff travels with laptops, connecting to the Internet from client sites, airports, coffee shops, and other points beyond the enterprise's control. These mobile devices must be protected while they are disconnected from the enterprise network by desktop antivirus software.
Also, although the majority of malware threats propagate through networks, they can still be transferred through shared storage devices. The earliest viruses traveled on floppy disks that were passed between PC users. Today, flash memory devices have largely replaced floppy disks as the preferred storage device for transferring data, but the problem remains the same: infected programs and documents can easily move from one computer to another. Desktop antivirus software can readily scan flash drives and eliminate known malware before it can infect another device.
Firewalls
Firewalls are the standard means for controlling the type of network traffic that enters and leaves an enterprise network. Firewalls are configured to allow traffic on necessary ports—for example, TCP port 80 for HTTP, 21 for ftp, and 23 for Telnet. When a service provided by a port is not needed, the port is blocked. Firewalls provide a first line, course-grained line of defense; finergrained security is required in addition.
The basic limit of firewalls is that they work with the structure of network traffic, not its content. For example, an infected file can be transferred into a network using ftp as long as the sender authenticates with the ftp server (assuming anonymous logins are not allowed) and the sender does not violate other basic constraints, such as exceeding storage limits. Similarly, a malicious application could use HTTP tunneling to transfer malware or use otherwise blocked protocols to communicate with malware already infecting a local device. This situation is especially problematic because of the high volume of HTTP traffic in enterprises. In one study of a large institution, more than 40 percent of all incoming and 90 percent of all outgoing traffic used HTTP.
Firewalls provide essential security functions but alone they are not enough. Secure content devices examine incoming traffic once it has passed the firewall (or before it reaches the firewall in the case of outgoing traffic). Rather than examine just the structure of the traffic (for example, "this is an SMTP packet"), it examines the content ("Lose weight while you work at home") allowing the secure content device to identify spam and other unwanted content. IPSs are closely related to firewalls.
Intrusion Prevention Devices
There are two types of intrusion prevention: host-based and network based. Host-based IPSs protect individual servers and workstations from attacks that cannot, or at least are not, stopped by perimeter defenses, such as firewalls. Host-based IPSs detect anomalous behaviors on servers as well as truly suspect actions, such as an attempt to write a file from a Web browser or the escalation of local privileges.
Host-based IPSs can do some things that other network-based approaches cannot. For example, a host IPS can analyze the content of an encrypted message after it is decoded; a secure content device that monitors network traffic does not have access to the decrypted traffic.
Network-based IPSs use signatures, or patterns of traffic, to detect anomalies in network activity. As with host-based IPSs, there are some attacks that are difficult at best to detect with other methods. One of these attacks is known as Address Resolution Protocol (ARP) poisoning.
ARP is used to map from IP addresses to MAC addresses, the unique physical address on a network interface. ARP, like other Internet protocols, is quite trusting. Devices do not need to authenticate to send an ARP message to another device; any device (or attacker) can send a message telling a server that IP address A maps to physical address B. The server will store that information in an ARP table and use the physical address when addressing messages to IP address A. With ARP poisoning, an attacker can effectively re-route traffic away from a legitimate device to another, compromised machine. Network-based intrusion detection can detect this type of attack in the lower levels of the OSI network model.
Complementing Secure Content
Both host-based and network-based intrusion detection provide defenses against particular types of attacks. Both protect information infrastructure, such as the integrity of network routing and the operating system (OS) access controls. These complement secure content devices that analyze the content that depends on that information infrastructure.
Policy Administration
The foundation of a secure infrastructure is a set of well-defined policies governing several aspects of information security, including:
- Authentication
- Authorization
- Vulnerability scanning
- Database access
- Remote access
- Password
- Wireless networking
Information security policy administration tools are relatively new but are emerging to address the difficulties in managing silos of security. One of the key reasons to use policy administration is to centralize management of policies and reporting. This complements secure content devices by providing the means to report on events and defined policies within the secure content device.
Deploying multiple defensive layers is a standard practice in information security. Some countermeasures, such as network intrusion detection and firewalls, protect the transmission of network traffic. Host-based intrusion prevention and desktop antivirus software protect the integrity of OSs, applications, and data. Secure content devices protect against the introduction of malware, spyware, spam, and phishing attacks from entering a network. Together these and other tools provide a security infrastructure that can provide a layered defense and address a multitude of threats.
What is the ROI for secure content appliances?
The Return on Investment (ROI) for a secure content appliance is based on a range of factors, including:
- Losing productivity of employees who have to deal with spam in their email accounts
- Additional hardware and software licensing costs to maintain adequate resources to process high volumes of email, including spam
- Losing staff time to eradicating and repairing damage caused by malware infections
- Avoiding fines for failure to comply with regulations
- Avoiding lost intellectual property when proprietary documents are transferred out the of the organization
Clearly, some factors are easily quantified, such as the amount of storage that is taken up with spam. Others, such as lost employee productivity, can at least be roughly estimated. However, some of the largest factors, such as regulatory fines and lost intellectual property are difficult to assess. Nonetheless, organizations can perform some basic ROI analysis on secure content appliances.
ROI and Related Calculations
ROI is one of a number of capital expenditure analysis calculations. Depending upon your needs, one or more of these calculations may be used to determine whether deploying a secure content device makes financial sense. The most commonly used calculations are:
- Present value—Present value is a calculation that takes into account the value of money over time. For example, if a company saves $10,000 in 1 year from an investment in IT infrastructure, and one can reasonably expect to earn 6 percent if that savings were invested (that percentage is known as the discount rate), then the present value of $10,000 a year from now is $10,000/1.06 (1 plus the discount rate), or approximately $9434.
- Net present value—The net present value is similar to present value but takes into account initial costs.
- Payback period—The payback period is the time period in which the total savings from an investment equals the amount of the investment. For example, a $25,000 investment that saves $10,000 per year has a payback period of 2.5 years.
- ROI—ROI takes into account both the net present value of money and the net benefits realized by the investment. Net benefits are defined as:
Savings + Increased Revenue – Recurring Costs
Without going into the details of why the calculation is defined as it is, here is the basic formula for calculating ROI over a 3-year period:
[Net Benefit for Year 1/ (1 + Discount Rate)]+ Net Benefit for Year 2/ (1 + Discount Rate)2 + Net Benefit for Year 3/ (1 + Discount Rate)3] / Initial Costs
- Internal rate of return—The internal rate of return (IRR) calculation is the most complex of the group listed here. IRR is often used to compare the benefits of different projects and choose among them. As IRR is expressed as a percentage, it is easy to compare projects of different financial and time scales. IRR calculates the discount rate at which the present value of the net benefit of an investment equals zero. (Microsoft's XIRR function and Star Office and Open Office's IRR function can be used to calculate IRR.)
For more information about IRR, see and "Internal Rate of Return Revisited" at http://members.tripod.com/~Ray_Martin/DCF/nr7aa003.html.
Calculating ROI on Secure Content Devices
To assess the investment value of a secure content device, you need to include in calculations the costs of spam, viruses, phishing attacks, lost productivity that result from non-business–related Web activity, violations of regulations, and loss of intellectual property. The last two items are difficult to estimate. The following example will ignore those values, as they are very environment dependent—thus, the results of the calculations may underestimate the true value of the investment.
The Cost of Spam
First, let's examine the cost of spam. There are basically three types of costs: lost productivity, additional hardware costs, and additional administrative costs. To calculate lost productivity, start with the number of email users, the average number of spam messages, and the time required to read and delete those messages. The basic formula for calculating lost productivity is:
Number of email users * number of spam messages per day PER USER* time in minutes to read/delete spam message * (average hourly rate / 60) * number of work days per year
To calculate storage costs, start with the number of email users, the average number of spam messages, the average spam message size, the number of days the message resides on the server, and the average cost of storage. The basic formula for calculating spam storage costs is:
Number of email users * number of spam messages per day per user* * average spam size * average cost of 1MB storage per year/ 365 * number of days message stored
To calculate additional administrative costs, you need to estimate the number of minutes per day email administrators manage spam problems and the hours per month, on average, email administrators and systems administrator spend addressing storage and network traffic–related problems as a result of spam.
With these three factors—lost productivity, additional hardware costs, and additional administrative costs—you can estimate the cost of spam to an enterprise. Figure 1.2 shows an example calculation of a payback period.
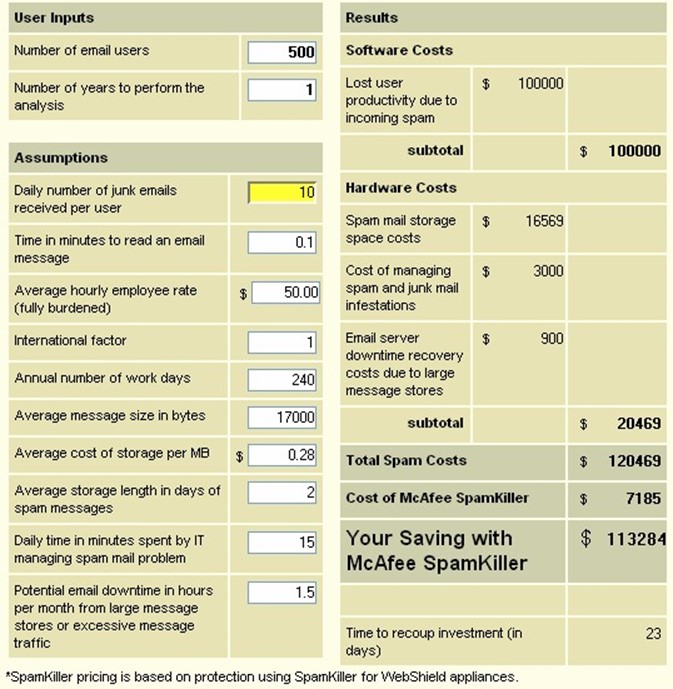
Figure 1.2: Example savings and pay-back period on one component of a secure content device—McAfee SpamKiller anti-spam software.
To calculate the ROI of this investment, simply take the net benefit and divide it by 1 plus the discount rate. Assume the net benefit is the savings on spam costs calculated in Figure 1.2, $120,469, the initial costs are $7185, and a discount rate of 6 percent. The ROI for this investment is:
ROI = ($120,469 / 1.06%) / $7,185 = 1581%
For every dollar spent on spam protection, $15.81 is saved. The cost of other threats to secure content are calculated in a similar manner.
The Cost of Viruses
Spam is constant, so users are always having to deal with it. Viruses, while still prevalent, do not present the same constant and sustained level of success in reaching targets. Therefore, one of the key factors in estimating the value of antivirus devices is understanding the probability that a virus will successfully infect an unprotected device. The other factors, which Figure 1.3 shows, are comparable to those used in the spam calculation.
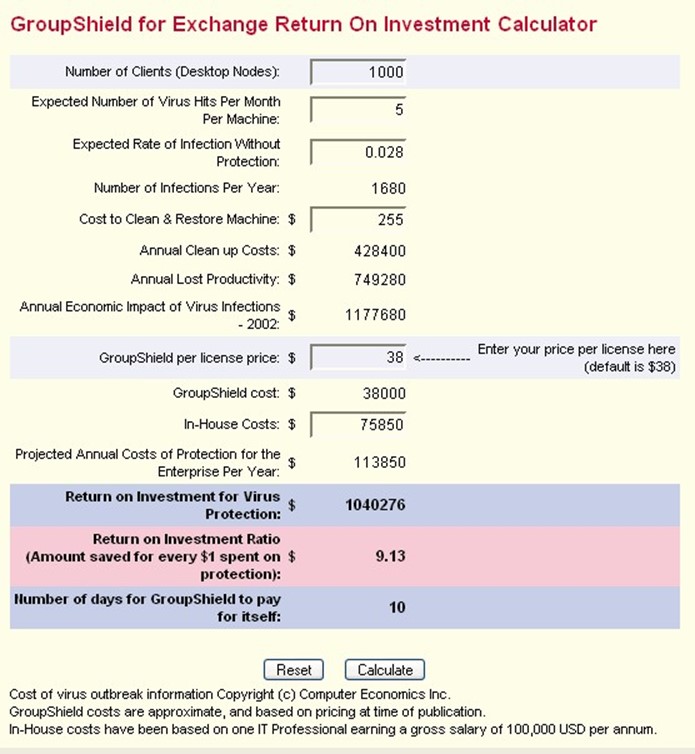
Figure 1.3: Example savings and ROI ratio for antivirus protection.
The Cost of Lost Productivity and Non-Business–Related Web Activity
Checking personal email, shopping online, browsing online casinos, and other non-business– related activities can put a drain on productivity. Secure content devices can prevent not only malware and unwanted content from entering an enterprise network but also users from browsing sites unrelated to business operations. Even a cursory examination of Web logs can give some indication of the level of this problem within an organization. How many users are visiting timewasting sites? What is the duration of time spent at those sites? With estimates of those two measures, you can calculate the expected savings in productivity by blocking those sites.
However, blocking sites does not guarantee that the time will be used 100 percent productively. When calculating productivity savings, consider using an adjustment factor to account for this fact.
The ROI from a secure content device is substantial even when considering only easily quantifiable measures, such as savings due to spam and virus protection. "Soft" benefits—such as avoiding regulatory fines and preventing the disclosure of proprietary and trade secret information—provide additional, but difficult-to-quantify incentives for investing in secure content devices.
How will secure content management aid in regulatory compliance?
For the past several years, governments have been actively changing the regulatory environment with respect to personal privacy and the integrity of business information.
Privacy Regulations
There has been growing concern over the use of private information for unauthorized business purposes. For example, should a pharmaceutical company know of a patient's congenital heart condition so that they can market a new cardiovascular drug? Should banks be allowed to share account information with business partners so that their partners can sell personal financial planning services? The consensus answer to these and similar questions is no. The widespread adoption of privacy protections has been rapid in the United States, the European Union, Canada and Australia. Some well-known regulations governing personal privacy include:
- State of California, United States passed SB 1386, a law directing companies and government agencies to inform California residents of any unauthorized disclosure of personal information.
- The United States passed the Health Insurance Portability and Accountability Act (HIPAA), which dictates how personal medical information is used and shared.
- The Australian Federal Privacy Act defines principals for the collection and use of personal information of Australian citizens.
- The European Union Directive 95/46/EC defines regulations about how personal data about European citizens is collected, stored, shared, and updated.
- Canada has passed the Personal Information Protection and Electronic Documents Act (PIPEDA) defining standards for protecting personal data.
The details of these regulations vary, but the objectives and requirements are similar. First, organizations must exercise due care when collecting and storing personal information. In some cases, regulations define the circumstances in which information may be shared. For example, under HIPAA, physicians can share information about a common patient but not with drug company sales persons. To limit a company's exposure with regard to privacy protection, most will implement access controls.
Access controls are physical and technical safeguards used to protect the integrity and confidentiality of data. Typical controls include access control lists (ACLs) and file protections that define which users may read and change data. Although these are essential controls, they are not always sufficient. Consider the following two examples.
Protecting Personal Medical Information
A hospital administrator receives a request from an executive steering a committee working on long range plans for hospital expansion. The committee needs aggregate information about the geographic distribution of patients and the types of medical services provided to patients from various areas. The administrator is pressed for time and cannot assign anyone to summarize the raw data; instead, he or she sends a database extract with detailed patient information, including personally identifying information. The steering committee is not making medical evaluations of those patients, so their detailed, personal information should not be shared. An access control system will not prevent this violation because the administrator has legitimate access to the data on a day-to-day basis.
What is needed in this case is a content-based control such as a content filter that can be configured to detect patterns indicative of personal medical records. For example, if data is frequently shared between systems in the hospital and with resident doctors' offices, there may be a standard program for extracting a patient record. This program may use a well-defined XML scheme with labels such as Patient-First-Name, Patient-Last-Name, and Primary-Diagnosis. These labels can be detected as data is transmitted across the network and, depending upon other conditions in the filter rules, the transmission can be blocked (see Figure 1.4).
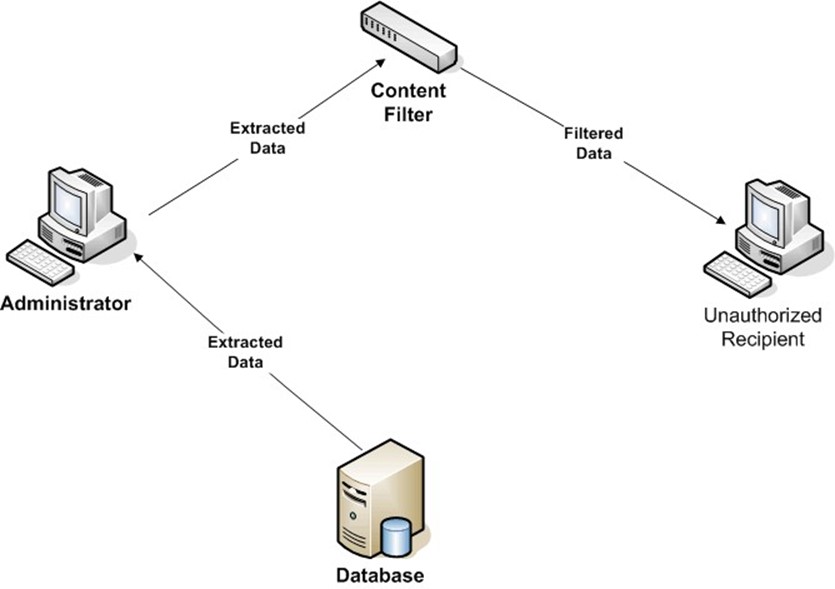
Figure 1.4: Extracted data analyzed by a content filtering mechanism can prevent the transmission of protected data.
In this case, there may be no intent to violate the regulation, the busy administrator just did not know that the extract with personally identifying information should not have been copied to others outside of the hospital's group of medical professionals. Not all violations are so benign.
Preventing Identity Theft
In the past, criminals robbed banks because that is where the money was. Now, stealing identities can lead to the money. Several high-profile security breaches of credit card processing and financial institutions are raising awareness of the threat of identity theft that results from poor security measures. Perhaps the most telling example to date is the exposure of as many as 40 million credit card accounts due to a breach at CardSystems, a one-time transaction processor for MasterCard, Visa, and American Express.
Businesses, governments, and other organizations with responsibility for protecting financial and personal data will often use several security mechanisms including access controls, firewalls, and intrusion detection systems (IDSs). Even with these safeguards in place, users inside the organization with knowledge of systems, patch levels, and application vulnerabilities can avoid security countermeasures and access confidential data. However, when that information is transmitted, it is subject to analysis by content filtering safeguards—preventing unauthorized transmission of protected data.
Filters could be constructed, for example, to detect patterns indicating credit card information being sent outside the organization—for example, a 16-digit number (credit card number) followed by a 4-digit number with the first two digits representing a number between 1 and 12 (the expiration date) being routed to an address outside the network (see Figure 1.5).
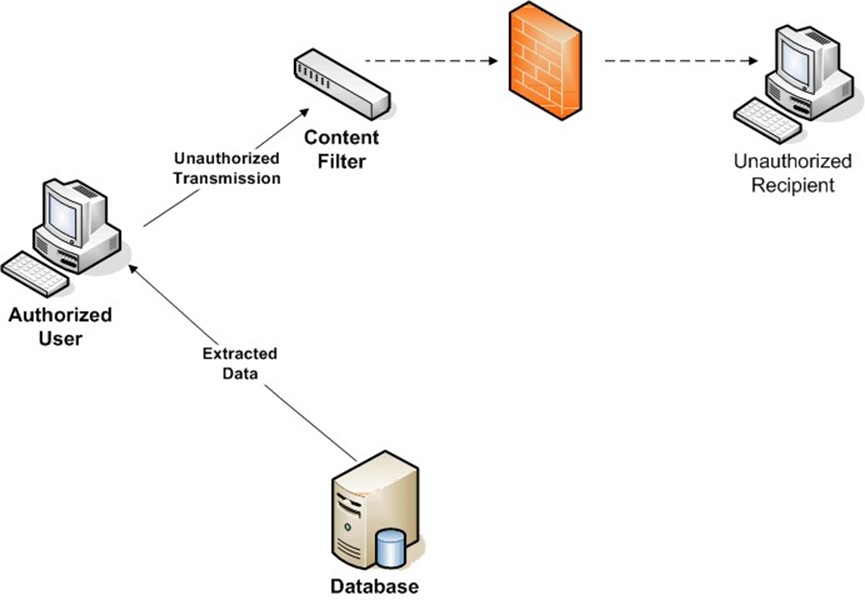
Figure 1.5: Depending on the content and the location of the recipient, a content filter can prevent protected data from being transmitted outside an intranet.
Security professionals have long known that no single security safeguard will eliminate threats to information systems and their data. Multiple countermeasures are required to reduce the wide variety of threats that are present today. Content filtering is one layer of a multi-layered defense against privacy violation as well as other compliance violations.
Data Integrity Regulations
Names such as Enron, Tyco, and WorldCom once elicited images of successful companies that set standards for performance in the market. Now they are more likely to conjure images of executives entering federal courthouses and stories of lost investments. Governments, especially the United States federal government, has reacted to these and other corporate scandals with laws designed to preserve the integrity of information provided to investors and other stakeholders in public companies.
The best-known regulation governing the integrity of business information is the United States' Sarbanes-Oxley Act. For IT professionals, Sarbanes-Oxley creates new demands for ensuring integrity of financial reports, for establishing internal procedures appropriate to ensure data integrity, and for reporting material changes in a company's operations. Other well-known regulations target particular industries, such as the Gramm-Leach-Bliley Act which applies to banks, and Title 21, Code of Federal Regulations, Part 11 (21 CFR Part 11), which applies to the pharmaceutical industry.
These regulations cover a broad range of topics but can be distilled to a set of core principals with respect to the due care that is required to protect information. Business must be able to
- Protect personal information with which they are entrusted
- Ensure appropriate security measures are in place so that data is not tampered with
- Establish well-defined controls and procedures for managing data
- Audit and report on changes to data under their control
Secure content devices can contribute substantially to the multiple layers of security measures that must be in place to meet these regulations.
The primary defenses for protecting privacy and integrity are access controls. Users should be granted permission to view and change data based on their role in an organization. However, primary defenses are not enough:
- Someone with legitimate access to confidential data might disclose his or her password to another employee, either accidentally or because of a social engineering scam (such as someone calling the user and pretending to be the Help desk).
- A vulnerability in a server operating system (OS) allows an attacker to gain control of the system and copy files with customer data or overwrite data such as financial projections.
- Spyware could include keyloggers, which record keystrokes (including usernames and passwords) and send the captured data to servers controlled by the perpetrators.
- A traveling executive might download information to an unmanaged device, such as a desktop computer in a hotel business center, which is locally cached. The data may be left for other users to retrieve without the executive's knowledge.
Secure content devices provide additional levels of protection in these cases. For example, in the case of the disclosed password, the unauthorized user may use the stolen credentials to log in remotely to a server. The unauthorized user may then attempt to download a file with customer names and credit card numbers. If the secure content device is configured to detect the proper patterns (for example, file headers, credit card number, key phrases, and so on), the file transfer will be blocked. The device could also block the transfer of data when an attacker exploits a vulnerability on a compromised server and attempts to copy sensitive information.
Spyware and keyloggers are especially menacing because large numbers of these threats can be deployed to automatically transmit significant amounts of information. Once the information is transferred to servers controlled by the perpetrator, text processing tools can be used to scan large amounts of data looking for valuable information, such as Social Security numbers, bank account numbers, and credit card numbers. Secure content devices can detect those same pieces of valuable information and prevent them from being transmitted in the first place.
What are best practices for educating users about spyware, spam, and phishing?
The first step in educating users about spyware, spam, and phishing is to explain the nature of the problem and the consequences of unwanted emails and programs.
Preventing Spyware Infections
In addition to using spyware blocking and removal tools, there are several steps users can take to reduce the chances of a spyware infection. These include:
- Properly configuring your browser—For Internet Explorer (IE), proper configuration includes disabling the Enable Install On Demand options (see Figure 1.6 for an example).
- Browse trusted sites—File sharing sites, such as music "sharing" sites, are likely spots for picking up spyware and other malware.
- Keep your browser and operating systems (OSs) up to date with patches.
- Use a firewall—Doing so can help prevent spyware from transmitting information from your computer.
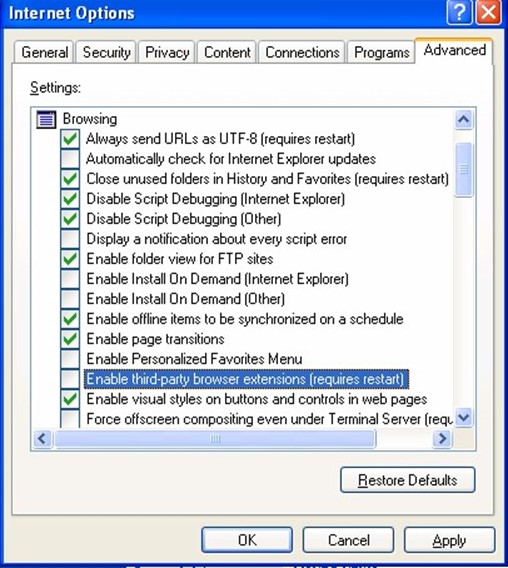
Figure 1.6: Configuring browser security settings is one step to reducing the chances of a spyware infection.
Mozilla Firefox, another popular browser, has fewer known vulnerabilities than IE and is thus a good option for security-conscious users. As with IE, Firefox users can disable the automatic installation of software, as Figure 1.7 shows.
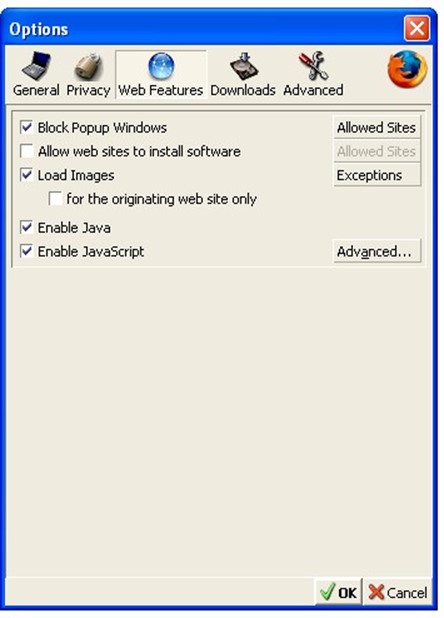
Figure 1.7: Firefox allows users to disable the automatic installation of software.
If the "Allow web sites to install software" option is selected, users can specify which sites are allowed to install software (see Figure 1.8).
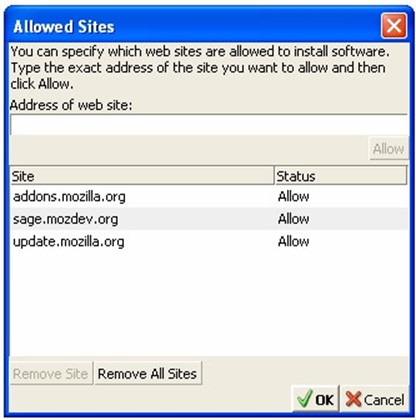
Figure 1.8: Firefox allows users to list rusted sites for the purpose of automatically installing software.
How to Reduce Spam
It's safe to assume spam will always be with us. Although spam filtering can be quite successful, reaching into the 90+ percent success rates for blocking spam, it's better to never receive spam in the first place. The following list highlights options for minimizing the amount of spam you receive:
- Do not add your email address to newsletters, opt-in offers, or other lists without understanding how your email address will be used. Reputable businesses and organizations publish and adhere to privacy policies. Make sure you understand an organization's privacy policy before giving them your address.
- Do not post your email on newsgroups or Web-based message boards. These sites are culled by spammers for email addresses.
- Do not respond to spam. A reputable mass emailer may take you off a list as requested but don't assume you are working with a reputable business if you don't know them. • Use a disposable email address when you must give an email address. If this disposable address begins to attract too much spam, drop the address.
Phishing attacks are a more troubling type of spam that warrant their own set of guidelines.
Phishing Facts Every Email User Should Know
Email users should understand the following about phishing attacks: • Phishing is a form of social engineering, otherwise known as a con. The phisher gains the confidence of their target and then elicits useful information.
- Phishers gain confidence of victims by appearing to be a trusted and legitimate entity, such as a bank or other business. It is relatively easy to steal logos and even entire Web pages from Web sites, so users should not be fooled by the well-known logo or look and feel of their bank.
- Rather than judge an email by appearance, examine the content closely. For example, is your bank emailing you that they need to verify your account number, Social Security number, or online banking password? If so, the message is most likely a phishing scam. When in doubt, ask yourself, has the bank ever called or sent postal mail with these questions? Chances are they haven't. Banks and businesses have other ways to verify their records.
- Beware of emails with upsetting or exciting messages. Phishers count on emotion to overtake rational assessment. If something serious has occurred with your personal finances, would a business email you about it? Not likely. When credit card companies suspect fraud, they call the home phone number of the card holder. • If you do decide to follow a link in an email, always type the URL into the browser. Doing so will help avoid any tricks used to exploit vulnerabilities in browsers. It will also make it more likely you will catch a minor difference in a legitimate Web address that links to a bogus site.
- Watch for promises of prizes, get-rich-quick schemes, and similar appeals to greed coupled with a request for personal information. (Spam sometimes makes similar promises but requires the recipient to purchase something in return).
- Spammers blanket thousands of email addresses, pretending to be EBay, Pay Pal, banks, and other institutions. Don't be surprised if you receive a phishing email from a business with which you have an account; phishers count on getting at least some customers from those businesses.
- Do not put personal or financial information in an email or Web site in response to an email. When in doubt, contact the business either by phone or through the business's Web site (by typing in the Web address or getting it from a search engine; don't use the URL in the email).
As with other security threats, phishing is a process of evolving threats and countermeasures. As email users become more educated about the nature and consequences of phishing, phishers have to hone their appeals. The latest evolution of phishing has earned the name "spear-phishing" because it uses low volumes but highly targeted phishing emails. This method makes these types of attacks more difficult to detect by businesses and more likely to fool the intended victim.