How to Spot Insider Threats Before They Wreak Havoc
Introduction
Everyone knows the classic horror movie plot: The heroes rush to barricade the doors and windows, only to discover that the monster is already inside the house.
If you're an IT security pro, you might want to watch one of these flicks again and reflect on how it applies to your job. Too many organizations today spend millions of dollars fortifying their perimeters to keep attackers out of their network — but fail to pay sufficient attention to the malicious users already inside.
Attackers are already inside, whether you know it or not. In fact, according to the Cyber Security Intelligence Index, insider threats represent 60 percent of all attacks. How quickly can you spot and block an employee or contractor who is misusing their privileges? What about an intruder using compromised credentials gleaned from a phishing attack? Or ransomware that's steadily encrypting your valuable files? As the minutes tick by, your risk of a costly data breach skyrockets. How costly? Well, the Ponemon 2017 Cost of Data Breach Study pegs the average cost of a breach at a whopping $3.62 million.
Insider threats represent 60 percent of all attacks. How quickly can you spot an insider abusing their privileges or an attacker using compromised credentials?
There are many solutions on the market that claim to help. But most of them follow a simple rule-based approach that drowns you in a flood of (mostly false) alarms that you have no hope of investigating. For example, in an effort to spot brute-force attacks, they'll alert you every time any user enters an incorrect password seven times in a row, even though most of those incidents are insufficiently caffeinated (or overly caffeinated) employees making typing errors or folks just back from vacation and unable to remember their credentials. To hone in on the true threats, a solution needs to take into account the broader context of a user's normal behavior and the current sequence of actions, not just an isolated event.
Change Auditor Threat Detection
Change Auditor Threat Detection is different. It uses machine learning and user and entity behavioral analytics (UEBA) to pluck out the activity truly indicative of a rogue user or compromised account from the vast sea of audit data. Then it shows you the most suspicious users and alerts so you can respond quickly and efficiently. Specifically, the solution establishes a baseline of each user's normal behavior — their usual logon times, what folders and files they typically access, the types of changes they make to Active Directory (AD), and so on. Then it uses unsupervised machine learning, user behavior analytics, SMART correlation and an array of predefined threat indicators to analyze subsequent user activity in real time and spot the true threats.
For example, in one actual 7,000-user environment, over a 45-day period, the solution distilled 46 million raw events down into just 42 risky users (see Figure 1).
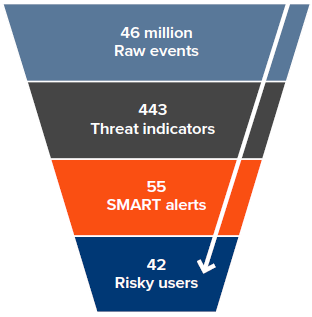
Figure 1. Change Auditor Threat Detection distills the vast sea of audit data down to a manageable number of SMART alerts and highlights the riskiest users in your environment.
This ebook describes nine of the most important patterns of suspicious behavior that Change Auditor Threat Detection can alert you to:
- Abnormal AD activity
- Brute-force attack
- Snooping user
- Data exfiltration or destruction
- Privilege elevation
- Scripted use of privileged account
- Abnormal system access
- Malware
- Lateral movement
Change Auditor Threat Detection identifies suspicious activity indicative of rogue users or compromised accounts — without drowning you in a sea of alerts.
Abnormal AD activity
Because of the critical role Active Directory plays in authentication, it's important to be able to spot suspicious user activity in AD. For example, attackers who gain highly privileged access to an Active Directory domain or domain controller can access, control or even destroy the entire forest, because any modifications they make to the AD database will be replicated to every other domain controller in the domain. And even less privileged accounts have access to sensitive data whose loss or exposure could damage your business and result in costly compliance failures.
Change Auditor Threat Detection can spot and score multiple indicators of abnormal AD
activity, including the following:
- A spike in the volume of changes to AD that a user performs compared to their individual norm, which can indicate that the account has been compromised and is being used to corrupt or destroy critical directory data
- Privileged users performing administrative actions that are not part of their standard routine, such as a first-level helpdesk rep who is responsible only for unlocking user accounts and resetting their passwords but who has suddenly begun creating new user accounts or changing group memberships
- Users making membership changes to sensitive privileged AD groups, which could indicate unapproved privilege escalation
- A significant spike in AD account changes, which could indicate an interactive privileged account being used to run scripts
- An abnormal number of failed AD changes, which could indicate an attacker attempting to exploit compromised credentials
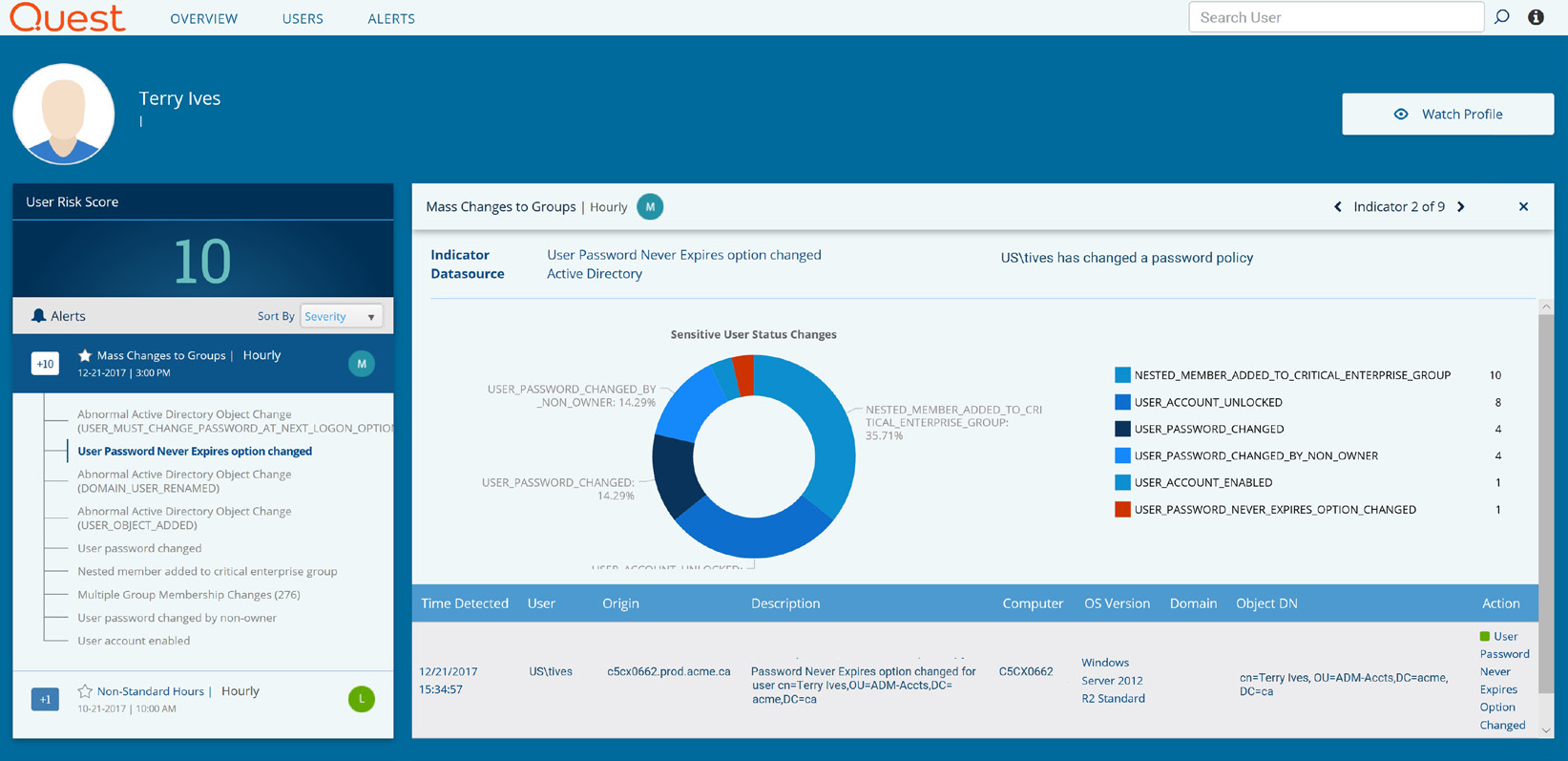
Figure 2. Change Auditor Threat Detection not only detects suspicious actions, like setting a password to never expire, but puts them in context of the user's other actions to assess the true risk.
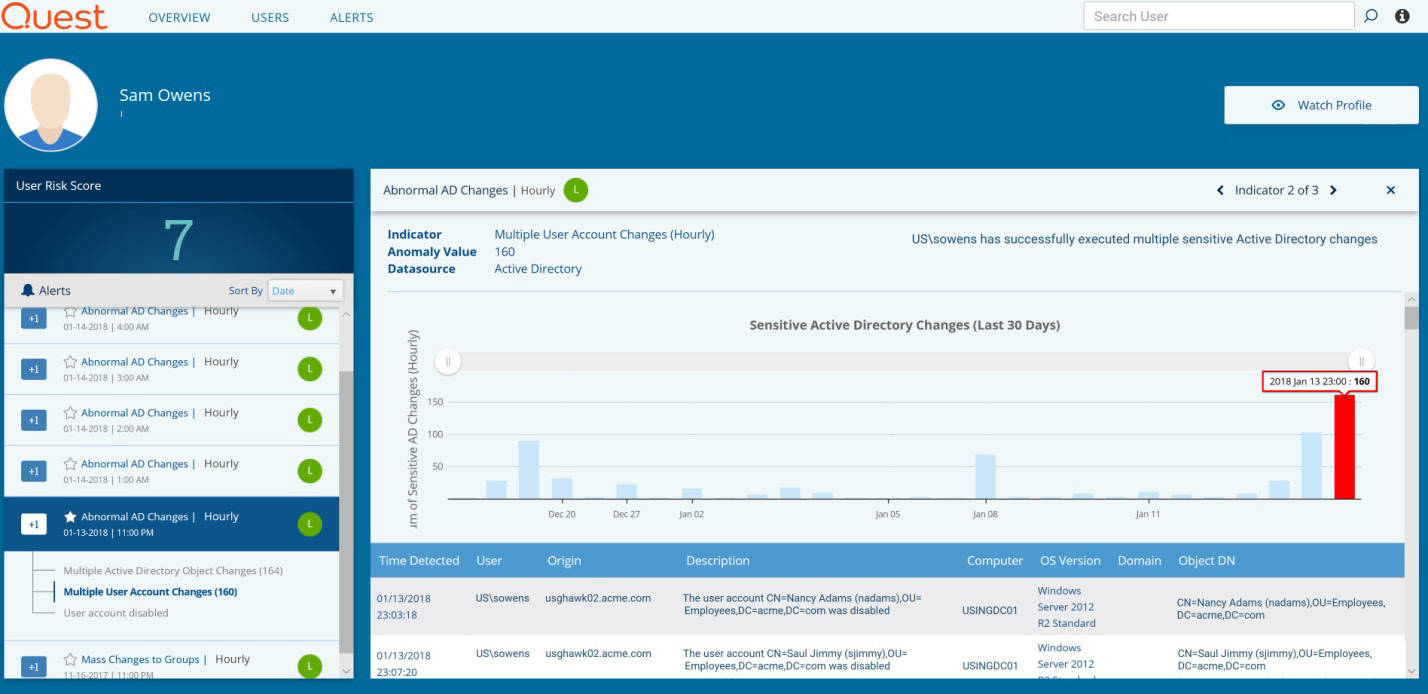
Figure 3. Change Auditor Threat Detection can spot spikes in AD activity that are abnormal for a particular user.
Brute-force attack
Brute-force attacks come in a variety of shapes. In traditional password cracking attempts, attackers repeatedly try to guess a user's password; they risk getting caught or being locked out after multiple failed attempts, but with some knowledge of the victim's password history, they might be able to successfully authenticate. Brute-force attacks can also be initiated from within the network by worms or other malware designed to identify user accounts and attempt to crack their passwords using password dictionaries.
However, you don't want to get an alert every time a user account makes multiple failed attempts to log on, because that doesn't always indicate that a user account is under brute-force attack. In fact, it is usually the result of a network configuration issue or a user entering their password incorrectly. That's why Change Auditor Threat Detection evaluates and scores threat indicators in the context of other anomalous activity, so that alerts are raised only when a pattern of truly suspicious behavior is detected, which dramatically reduces false positives.
Moreover, each brute-force alert that the solution raises includes all the context of the security events that triggered it, so it's easy to investigate where the authentication attempts originated and whether it is simply the legitimate account owner attempting to log on.
By correlating failed logons with other user actions, Change Auditor Threat Detection can alert you to true brute-force attacks without drowning you in false positives.
Snooping user
Snooping is unauthorized access to data. For example, an internal user who is inappropriately curious might attempt to browse servers and folders that they shouldn't be accessing, such as salary information or reorg plans. An actively malicious rogue employee might actively try to locate and steal valuable corporate information for personal gain or other reasons. More sophisticated snooping methods use software programs to remotely monitor activity on a computer or perform automated discovery of file resources.
Change Auditor Threat Detection highlights not only failed attempts to access data a user clearly does not have permissions for, but also successful attempts to access data that is outside of the user's proper purview but where permissions may not have been set restrictively enough.
Indicators of this activity include:
- A high number of file access attempts in a short period of time
- A high number of failed file access events
- Attempts to access file servers and folders the user has rarely or never accessed in the past
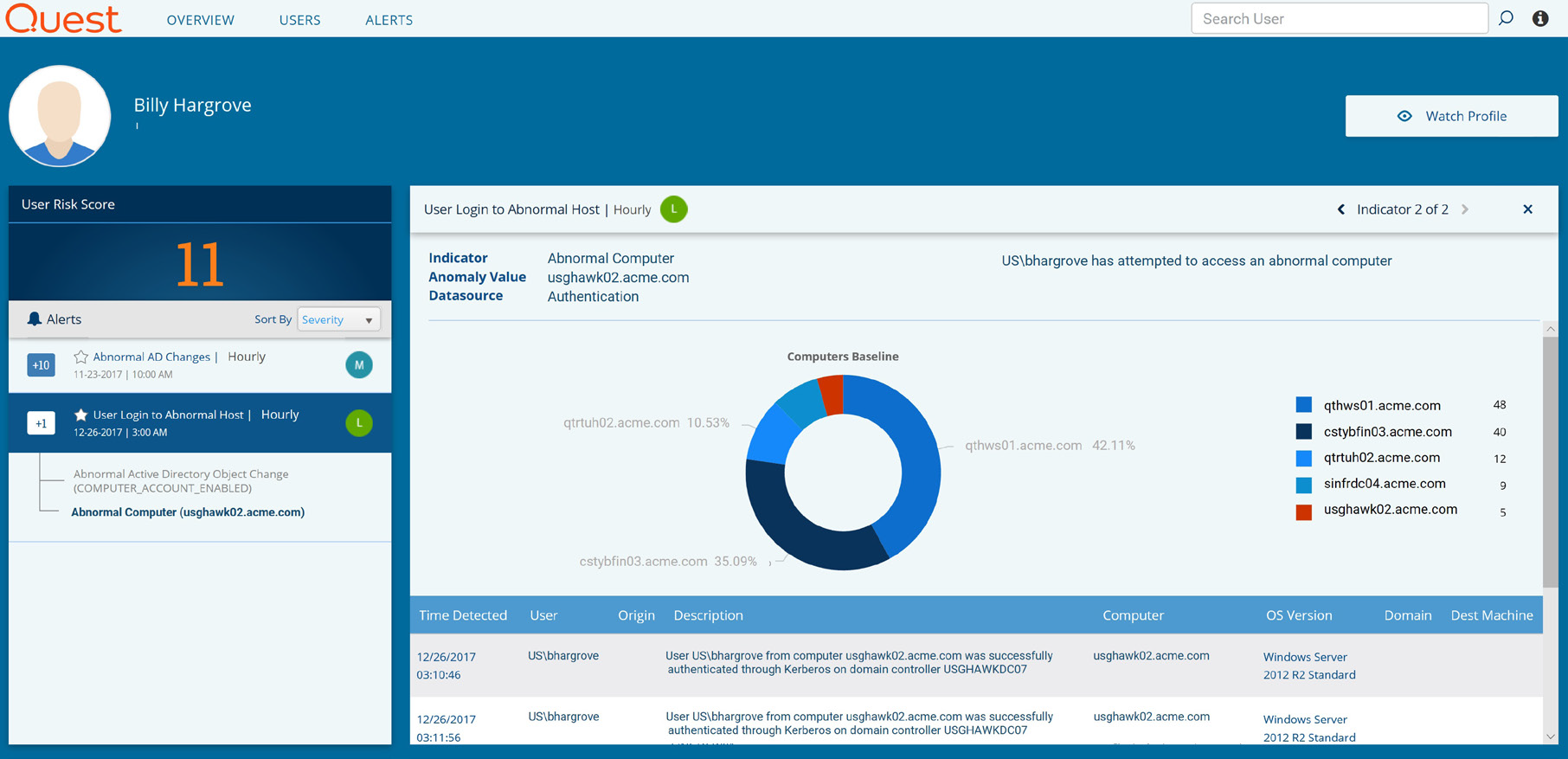
Figure 4. Change Auditor Threat Detection alerts you to users attempting to access data they don't have permissions to view or that is outside their normal responsibilities.
Change Auditor Threat Detection alerts you to users attempting to access data they shouldn't access.
Data exfiltration or destruction
Data exfiltration is the unauthorized copying or transfer of data from a computer or server using any of multiple techniques. While data exfiltration is often executed by cybercriminals over the internet, rogue employees also steal valuable corporate data in order to use it themselves, take it with them to a new employer, leak it to third parties or sell it to criminal organizations. Disgruntled or former employees may be more interested in destroying data than in stealing it, in the hopes of wreaking havoc on the organization.
Indicators of this activity include:
- An excessive number of file access or file move events, which can indicate that sensitive files are being copied from a server
- An excessive number of file delete events, which can indicate the malicious destruction of data
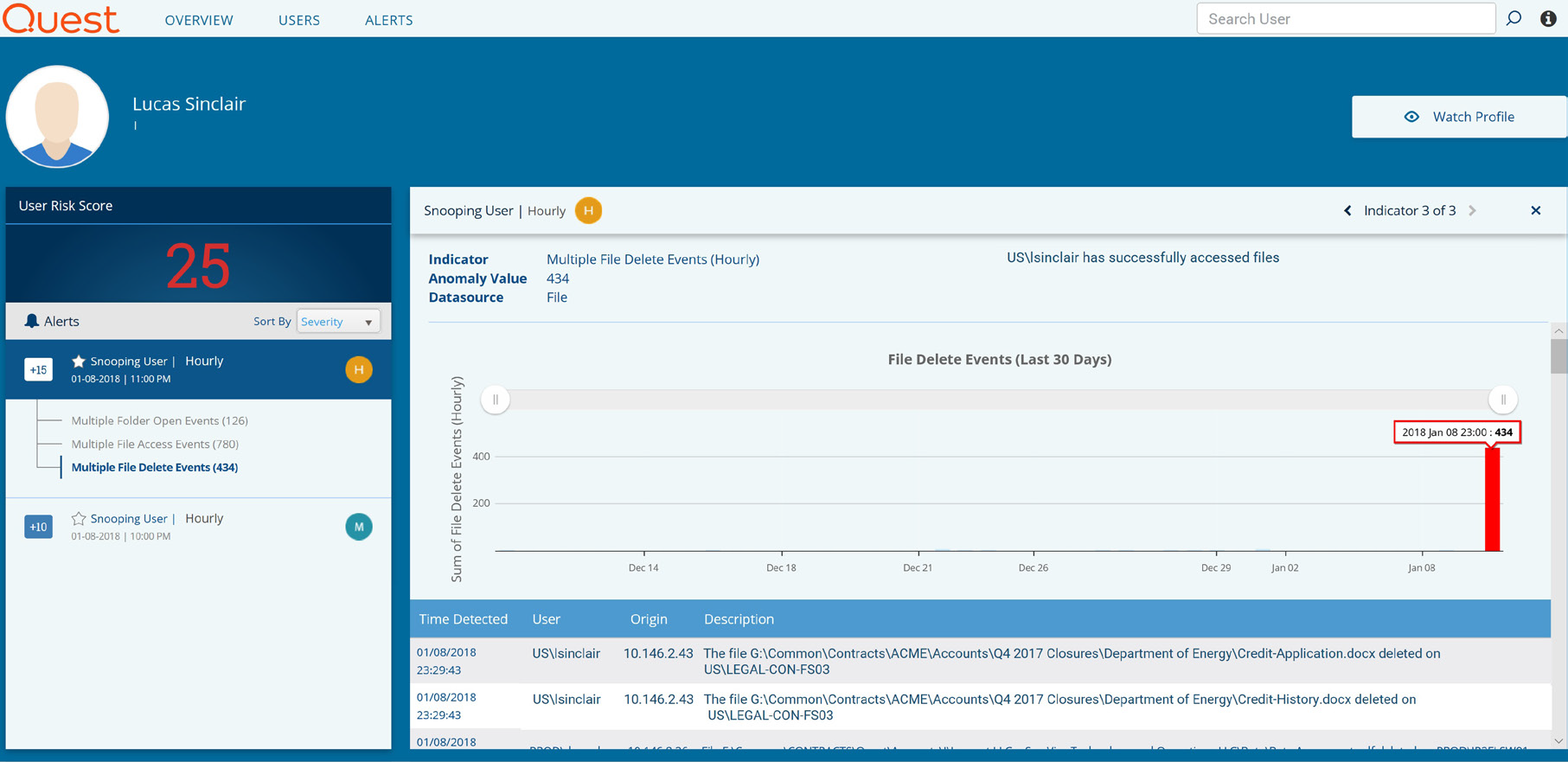
Figure 5. Change Auditor Threat Detection pinpoints users who might be attempting to steal or destroy your valuable data.
Change Auditor Threat Detection identifies users who might be attempting to steal or destroy your data.
Privilege elevation
Attackers often gain a foothold in the corporate network using regular user accounts, which are usually easier to compromise than admin accounts, and then elevate the privileges of those accounts in order to get access to the data or systems they're interested in. Similarly, rogue insiders often attempt to elevate their own privileges, or get the access rights they want through the more surreptitious route of creating a new account and adding it to a nested privileged group.
The addition of a user to a privileged group should always be monitored closely, but most of those events are legitimate. Change Auditor Threat Detection highlights the truly suspicious events by correlating the addition to a privileged group with related suspicious activity. For example, if just before a user created a new user account and added it to a privileged group, they logged on from an atypical location after failing to authenticate multiple times in a row, you'd see this alert at the top of the list to enable prompt investigation.
The primary indicators of privilege elevation are:
- A user being added to a critical built-in privileged group, either directly or via nested group membership
- A user being assigned elevated permissions directly
To spot improper privilege elevation, Change Auditor Threat Detection considers each event within the broader context of the user's related actions.
Scripted use of an account
Sometimes the volume of activity by a given account is so high that it clearly could not be performed interactively by a user, and therefore it is likely that a program or script is operating under a user's credentials, perhaps to make mass destructive changes to AD or valuable file data.
A better designed program or script might take over a user account and work more slowly in order to avoid triggering a simple threshold-based alert. But even that tactic wouldn't help it get past Change Auditor Threat Detection. The solution constantly compares a user's current behavior
to their individual stored baseline, so an abnormal number of access or change attempts would be quickly flagged as a probable attack.
Indicators of this activity include an excessive number of successful or failed attempts to:
- Change users or groups in Active Directory
- Access, move or delete files
- Authenticate using different user accounts
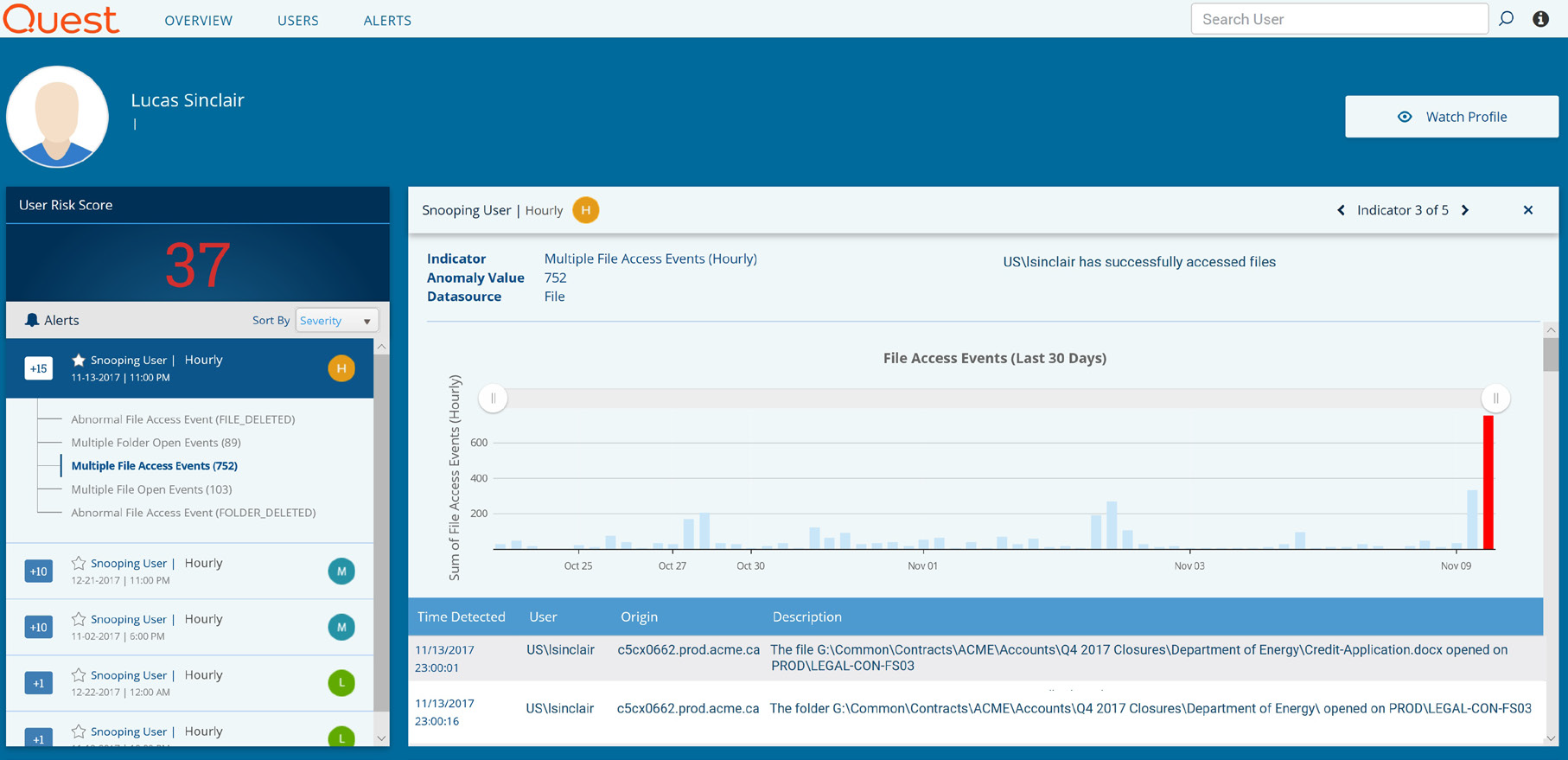
Figure 6. An abnormally high number of file access attempts by a user account could be a sign that a program or script is operating under that user's credentials.
An abnormal number of access or change attempts can be a sign that a user's credentials have been taken over by a program or script.
Abnormal system access
If a user account accesses your network from an atypical geographical location or an abnormal workstation, it could be a sign that an external attacker has been able to compromise the account. However, most of the time, it is not an attack at all, so raising an alarm on all abnormal access events would quickly drown you in a sea of dead-end alerts.
Change Auditor Threat Detection, however, correlates the unusual access location with subsequent suspicious activity, such as snooping or making abnormal changes to AD. That is, the anomalous access location provides additional context that raises the score of the other alert, so you know to investigate it promptly.
Indicators of this activity include:
- A user attempting to authenticate from a workstation they rarely or never used before
- A user attempting to log on from a geographical location that is abnormal for them or for the organization
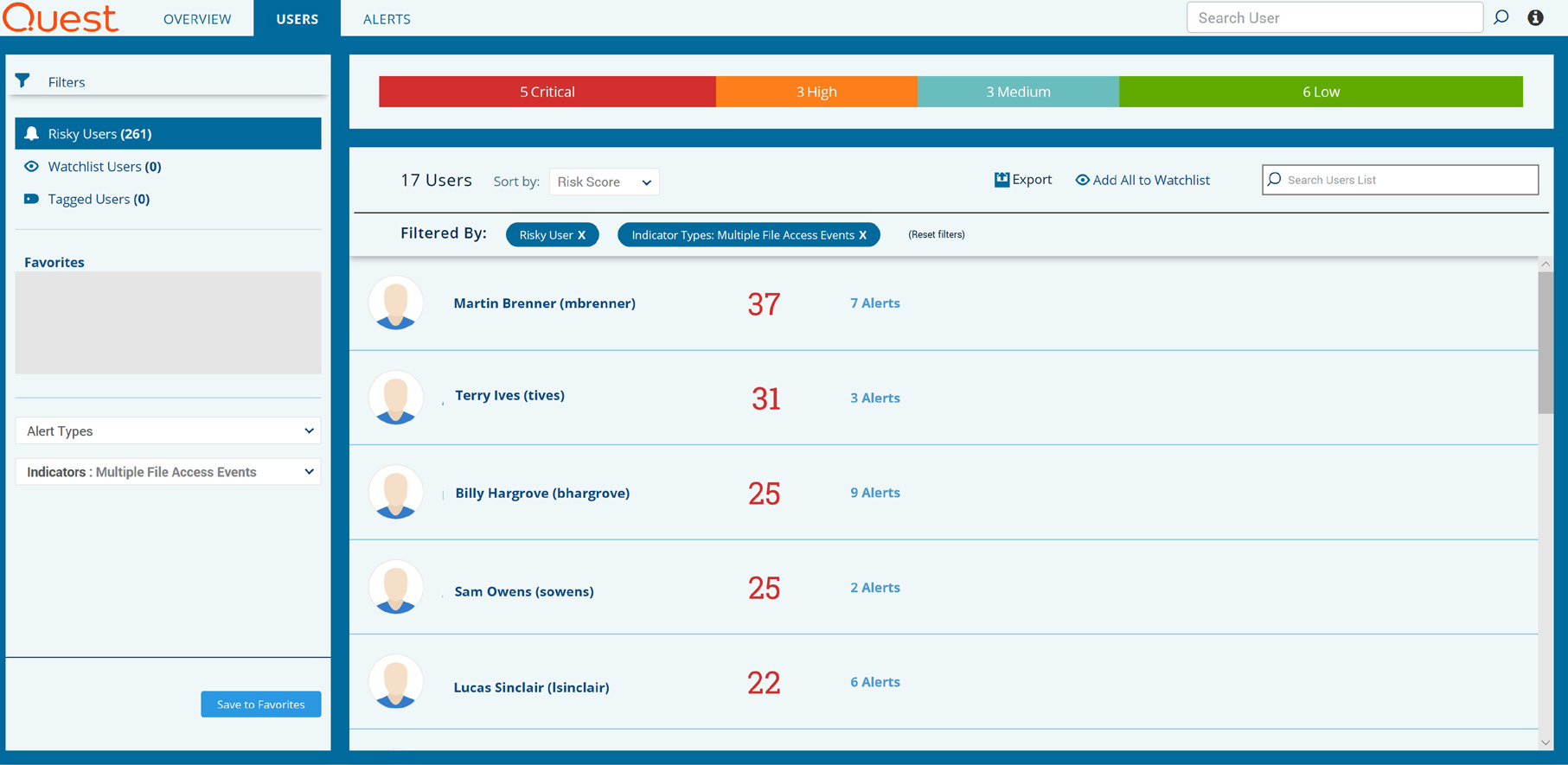
Figure 7. Change Auditor Threat Detection displays a dynamic list of the most suspicious users and user behaviors detected in the environment.
Access from an atypical location increases the likelihood that the user's suspicious actions are actually a threat.
Malware
External attackers and disgruntled, rogue or careless employees are not the only threats you have to worry about. As recent headlines make clear, organizations are also under attack by ransomware and other forms of malware. Once such a program has established a beachhead on a particular computer, it will attempt to compromise user accounts in order to gain access to all the resources those accounts have permissions for.
Malware can take over user accounts and use their privileges to steal, encrypt or destroy valuable data.
Indicators of this activity include:
- An excessive number of attempts to log on to multiple user accounts, all from a single computer or IP address
- An excessive number of attempts to log on to multiple servers, domain controllers and domains, all from a single computer or IP address
- An excessive number of file renames across multiple folders and servers, all from a single user account
Lateral movement
Once attackers gain access to your network (via stolen credentials, brute-force attack or some other method), they will start attempting to log on to your various servers, looking for valuable data to steal and additional credentials to compromise. They usually have plenty of time to locate and take what they want; the Ponemon Institute's 2017 Cost of Data Breach Study found that the average time to identify a breach is 191 days — more than six months. And it takes another two months (66 days) to contain the breach.
On average, attackers lurk in the network for more than six months before being detected.
Because Change Auditor Threat Detection maintains a baseline of normal behavior for each user, and pieces together patterns of behavior instead of looking only at isolated events, it can quickly spot accounts that have been taken over by imposters. Those accounts will be highlighted in the threat dashboard, so you can quickly take action to protect your valuable assets.
Indicators of this activity include:
- Multiple failed or successful attempts to log on to different servers 66 dashboard, so you can quickly take action to protect your valuable assets.
- Attempts to access servers that the user rarely or never accessed before
- Multiple user accounts logging on from the same computer or IP address
On average, attackers lurk in the network for more than six months before being detected.
Conclusion
IT environments today record literally millions of raw events each day. Most of those events represent perfectly normal and legitimate activity — but you'd never know that given the flood of alerts that most threat detection solutions generate. Analysts waste precious time chasing down false positives while attackers and malicious insiders go unchecked.
Change Auditor Threat Detection cuts through the noise and pinpoints the true threats in your environment. By understanding which patterns of behavior are normal for a given user and using a host of predefined threat indicators, the solution accurately identifies suspicious activity that could be indicative of a brute-force attack, data exfiltration, privilege escalation, malware or other common attack scenarios.
To learn more, please visit www.quest.com/threatdetection