Managing and Governing Identities in the New Open Enterprise
Welcome to Your New Reality: The Open Enterprise
The proliferation of SaaS apps and mobile devices makes network security an increasingly complex challenge. Your employees and partners now have unprecedented levels of access to your organization, often from outside the physical boundaries of the enterprise. That means your perimeter security won't cut it anymore – identities have become the new perimeter.
Not only is the number of users increasing, they demand convenient access to content and apps from anywhere, at any time, on any device. Meeting those demands is difficult enough. Doing so without putting security at risk represents an enormous challenge. There are several steps your IT organization can take to successfully leverage the open enterprise and grow your business in a safe and secure manner.
New Technology Means New Identity Management and Governance Challenges
The new open enterprise makes managing user identities and entitlements more difficult than in the past. Robust perimeter security used to be sufficient. Now, the increasing number of users—many of whom have been granted excessive privileges—creates an entirely new set of vulnerabilities that can be more easily exploited from remote locations than ever before.
Among the immediate identity management challenges facing your IT organization is determining how to:
- Eliminate "privilege creep" through ongoing automated certification of all user access
- Automate identity processes to replace costly, error-prone manual processes
- Simplify identity lifecycle management through increased automation
- Improve employee productivity by eliminating time-consuming, paper-based certifications
- Simplify the user experience by streamlining access to apps, enabling self-service and supporting mobile users
- Support both cloud and on-premise environments with faster, more flexible deployment option
It's All About the Business User
As the keepers of the keys, IT organizations have traditionally chosen identity management solutions that make their jobs easier—without giving much consideration to their impact on business users. But, by delivering an inconvenient and inefficient user experience, IT could be hindering business productivity and growth.
The ideal solution creates a bridge between IT and the business, creating a convenient, intuitive "one-stop shop" for business users to obtain services and information from the identity management system.
Business Users – Business-Focused
- Demands convenient and simple interfaces
- Requires consistent experience across Web and mobile
- Needs to interact in business terms
IT Users – Technology-Focused
- Tolerant of inconvenient user experience
- Often does not require mobile access
- Is comfortable interacting in IT terms
Managing Identities in the Age of the Open Enterprise
As apps have moved to the cloud, and user identities have become dispersed across disparate systems, managing identities and access has become more challenging. The days of managing internal users who only have access to a limited number of enterprise systems and apps are over. The new model requires flexibility, automation and a business-orientation that are beyond the capabilities of most existing identity management solutions.
Effective identity management and governance in the open enterprise must address:
- Employee lifecycle management – A streamlined process for managing user identities and entitlements from onboarding to termination
- Access request and approvals – The ability to provide a convenient, intuitive experience for access requests and approvals
- Certification campaigns – Automated user access certification
- Risk analytics – Detection and prevention of excessive privileges and segregation of duties violations
- User experience – Convenient access for users, across all platforms and devices
- Customized interfaces – An intuitive experience for all users, based on their unique role and the branding needs of the organization
Employee Lifecycle Management — Improving Efficiencies and Reducing Risk
The open enterprise has greatly complicated the process of managing users and their access across different populations, as well as across on-premise and cloud applications. To provide a unified and comprehensive approach, this process must be treated as a lifecycle – beginning with onboarding and ending with the termination of the user's employment.
Factors that separate a leadership solution from a merely adequate one includes:
- Breadth of provisioning connectors
- Extensive role discovery and privilege clean-up capabilities
- Identity analytics and reporting
- Business-orientation of the user experience
- Tools to simplify deployment management and connectivity to enterprise applications
Simplified Identity Management and Governance Lifecyle

Access Requests and Tracking – Simplifying the User Experience
Requesting access to applications or role assignments can be a painful process. Being forced to communicate in "IT-speak" rather than business terms and models makes things all the worse. Users need to be able to easily request access in an intuitive and understandable fashion. An effective access request system must provide:
- A convenient "shopping cart" experience for requesting access and roles
- User empowerment through robust self-service capabilities
- A business-friendly entitlement catalogue
Meanwhile, the absence of an intuitive, automated request tracking and approval system can waste managers' valuable time. Inflexible workflow processes can further hinder your organization's ability to support its dynamic business needs.
You need access tracking capabilities that provide:
- Flexible workflow models, including elements such as delegation, priority ratings and more
- Summary reports on the status of all requests, highlighting overdue and higher risk requests
- Entitlement analytics identifying Segregation of Duties violations
Certification Campaigns – Simplifying Audits and Reducing Risks
Access certification is a pain – but it's necessary in order to validate compliance with policy and regulations.
But, simply eliminating spreadsheets and manual processes isn't enough – certification campaigns need to be highly flexible and oriented towards the needs of the business.
You need certification capabilities that support all of these types of campaigns:
- Entity – certify the access rights associated with selected users, role or resource entities
- Recertification – repeat the certification process based on a previous campaign.
- Differential – certify entitlements which have changed since a previous campaign.
- Self-attestation – certification performed by users, rather than a manager or resource owner
It is true that a simple certification ("Should this user have access to this resource?") often requires additional contextual information to help managers certify access accurately. For example, how frequently a user has accessed a resource, the last time of access, or suspected improper access rights can be highlighted to help make better, faster certification decisions.
Risk Analytics – Preventing the Next Data Breach
As your organization expands, roles and entitlements can start to overlap and proliferate. And as "entitlement creep" occurs, policy violations and overall risks abound. Risk analytics can provide key information to help you identify and remediate these threats quickly.
These analytics can be static (such an offline role discovery and analysis process) or real-time (highlight segregation of duties violations at the time of assignment). A comprehensive approach to identity risk should include both approaches.
Good identity analytics help minimize risk by enabling you to:
- Clean up excessive and erroneous access rights
- Discover and create new roles based on existing entitlements
- Correct entitlements that are out-of-pattern relative to other users with the same roles
- Detect overlapping or redundant roles
- Detect and prevent segregation-of-duties violations during provisioning
The User Experience – The Key to Effective Identity Management
To improve user productivity and satisfaction, your identity management solution must successfully engage the business user with an experience that is intuitive and convenient. That means:
- Talking to users in a language they understand
- Supporting the devices business users prefer
- Making the interface easy—and even fun—to use
Business managers need a similarly convenient process to track and act on their employees' access requests. And your system must interact with them in concepts and terms that are familiar to them.
The trick is to provide the convenience and ease-of-use that business users demand without sacrificing the robust capabilities that help your IT team meet its obligation to ensure security and efficiency. Capabilities such as deep provisioning, risk analysis, identity analytics and complete identity lifecycle management are all critical in the dynamic identity environment of today's complex, open enterprise.
A look inside an ideal access request process. An intuitive "Shopping Cart" allows users to:
- Conveniently select roles and entitlements needed to perform their job duties,
- View current access privileges
- Easily view the status and progress of previous access requests
CA Delivers the Most Comprehensive Identity Management Solution for the Open Enterprise
The CA Identity Suite enables your businesses to uniformly govern access to applications and services across cloud and on-premise IT environments. By automating such IAM functions as user provisioning and entitlement certification, you can reduce security management costs and improve employee productivity.
The Identity Suite also includes an Identity Portal, providing an intuitive, business-oriented user experience designed to dramatically simplifies the process of managing user identities, access requests and approvals. In addition to the Identity Suite, CA offers Privileged Identity Management to enable you to manage shared accounts more securely, while providing fine-grained controls over the actions of privileged users.
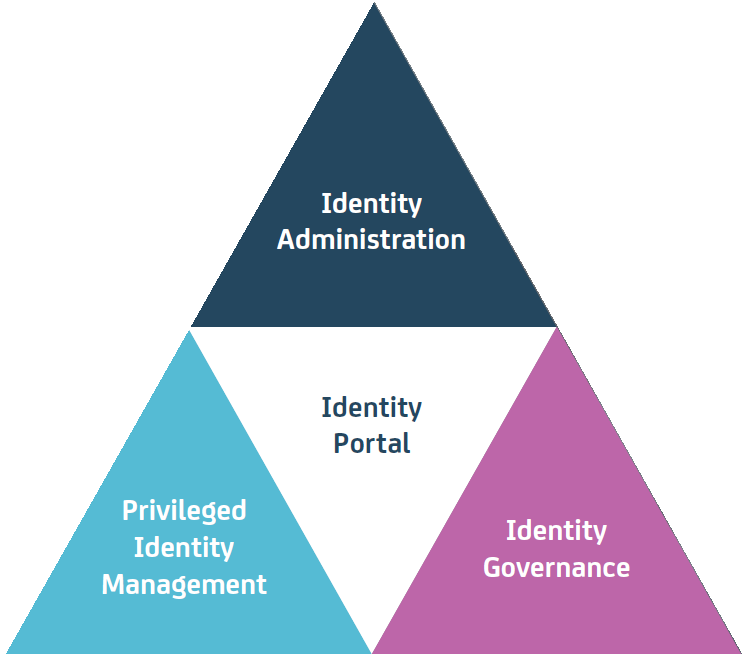
Identity Administration
- Automated provisioning
- Policy management
- Password reset
- Self-service
Identity Portal
- Business User Experience
- Single pane of glass for IM & IG
- Access Request
- Risk-Awareness
Privileged Identity Management
- Shared account password management
- Fine-grained access controls
- Session Recording
Identity Governance
- Access Review/certification
- SoD analysis and decision support
- Role modeling
- Entitlement cleanup