You can get Identity and Access Management right
Introduction
In an ideal world, we'd have the budget and time we need to get things done. And tomorrow would be predictable. But that's simply not the case, especially in the IT universe.
As you well know, the world of identity and access management (IAM) is one of constant change, shrinking deadlines, minuscule budgets, overtaxed staff and unmerciful regulations. Unfortunately, the approach most organizations take to IAM involves piecing together 'half solutions,' in the hope that tomorrow's solutions will address real-world needs.
In this book created exclusively for the RSA Conference, we will evaluate what IAM done right would, should and can look like. It delves into the most pressing IAM issues faced by virtually every organization and offers actionable, affordable and sustainable approaches to the IAM challenges you face. At One Identity, we help you achieve your IAM objectives and get IAM right in a way that moves you and your business towards your goals.
We hope you find value in our book, You Can Get Identity and Access Management Right, as we take a look at the fundamentals of IAM and then highlight key topics and solutions that apply to Identity Governance, Access Management and Privileged Access Management.
Conventions
Throughout this book, we've used a number of conventions to help highlight important points, provide supporting evidence, or advise you of our obvious bias.
Look for the following conventions:
- Real-world example – Stories of real organizations, facing real challenges, and really solving their problems (often the names have been changed to protect the innocent)
- Facts and figures – Research- based information that supports principles discussed throughout the book
- Techie alert – Definitions and terms used in the identity and access management industry that may not be familiar to you (Then again they might.)
- Useful tip – Information that will help you easily achieve things discussed throughout the book
- Blatant sales pitch – Where we get to say why we actually wrote this book. It may be a little biased, but we suspect that the reason you're reading this book is to find solutions to your challenges. This is where we give them to you.
Identity Governance – the path to agility
How often do our efforts at governance seem like the futile attempts of the Spinal Tap band members to find their way to the stage? And how often do we, in spite of our best intentions and efforts, find ourselves wandering through the maze of our organization, hoping to stumble across the stage door that leads to identity governance?
For our discussion, governance is defined as business-enabling activities that move technology beyond simple efficiency tools into the realm of confidently and correctly providing access and performing administrative activities. This also means all this is done with the full knowledge and endorsement of the organization, while satisfying any internal or external regulations. Providing all these requirements are met, governance acts as the framework for how those activities should be done.
Put simply, governance is ensuring that:
- The right people…
- Have the right access…
- To the right resources…
- At the right time…
- In the right way…
- With all the other right people knowing what's going on and saying it's okay
In a perfect world, getting it right would be easy. The risks of inappropriate access or activity would be minimal because all of it would be controlled by the right people with complete visibility into proper ownership and responsibility. Your organization could easily satisfy compliance requirements. If an auditor asks for information, or you need a periodic entitlement recertification, you could generate an accurate and user-friendly report with just a few mouse clicks. But, unfortunately, we don't work in the perfect world. We work in the real world where getting it right never happens by accident.
For most organizations, governance is a major challenge. In fact, governance can't even be considered until access, security, control and management have been achieved. If simply provisioning access is difficult, leveraging that access to enable business agility – the goal of governance – is impossible. If all your time is spent remedying a forgotten user password, for example, how are you going to ensure that the correct controls are in place so that the user had the appropriate access in the first place? And that's just a couple of components of being compliant. The real challenge is proving compliance. It's a complex situation.
Several key governance factors are involved in a typical audit. They may take different forms, but it all boils down to:
- Provisioning – making the process of thoroughly and correctly granting access across the entire environment as efficient as possible. This includes the more important security-related action of de-provisioning. While provisioning itself is an access management activity, without provisioning done right, governance is impossible. To complicate things further, the resources that must be provisioned, and therefore governed, have expanded beyond the typical control of the organization and into the world of the cloud and digital transformation
- Workflow – showing the steps from access needed to request to fulfillment, ensuring compliant processes are followed throughout
- Attestation – fulfilling the periodic requirement to review all access entitlements (or rights) and certify their appropriateness
- Policy – documenting and enforcing the underlying rules that govern user access to applications and data, as well as showing that those rules comply with established regulations
- Approvals – ensuring all the right people approve access requests before it is fulfilled
- Risk discovery and management -- a key component of achieving a governed state is to find and remediate areas of risk. From an IAM perspective, this is most often associated with instances of individual ownership, rights, and responsibility being out of alignment with what is expected or appropriate for the individual
While access management is primarily concerned with simply getting things done, governance addresses getting those things done the right way.
"It's a wall!" The trunk was identified as a snake, the leg as a tree, the tusk as a spear, and the ear as a fan. We'll pretend that none could smell or hear… but that's beside the point. Each person's perception of the elephant was limited to what they were able to experience directly.
The elephant in the room
There's an old story about a group of blindfolded people being let into a room with an elephant and asked to identify it based on only what they can feel with their hands. One felt the elephant's tail and declared, "it's a rope." Another, feeling the elephant's side stated, "It's a wall!" The trunk was identified as a snake, the leg as a tree, the tusk as a spear, and the ear as a fan. We'll pretend that none could smell or hear… but that's beside the point. Each person's perception of the elephant was limited to what they were able to experience directly. Governance is similar.
It seems that the default approach to governance is limited to what an organization is experiencing at the time, or what they are able to most easily comprehend, measure and control. For many, governance may be confined to the narrow scope of satisfying the auditor's finding of the day. For others, governance may be influenced by a specific security breach or incident. And to still others, governance may be focused on the organization's 'crown jewels,' those applications or data sets that are the most important to achieving business agility. All are absolutely appropriate and all are equally important. However, just like the elephant in the room of the blindfolded, a narrow focus will leave out critical pieces of the bigger picture.
Therefore, governance must be concerned with the whole of IT, not just the easy parts. To get governance right you should be focused on:
- User access to all applications
- User access to all types of data: on prem, cloud, and as-a-service
- Administrator access to all systems: on prem, cloud, and as-a-service
The root of the problem
The challenges associated with governance are all too common in today's highly complex and security-conscious landscape. Basically governance can be illustrated by a 'closed loop' model.
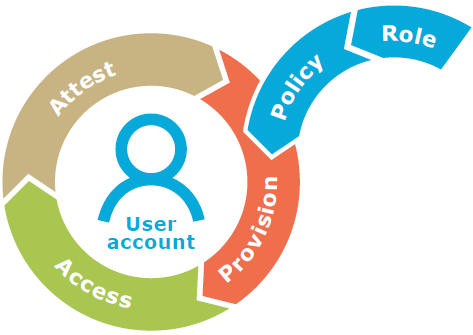
Figure 1. A closed-loop model for governance
As discussed earlier, each system requires access; therefore, each system can be subject to governance. Access is the result of provisioning that is controlled by policy and streamlined through the use of roles or other attributes. Compliance demands attestation to the appropriateness of the access, which in turn feeds into continued maintenance of the identity lifecycle for continued access. The operable word here is 'each' system.
The four fundamentals of IAM are authentication, authorization, administration and audit. Just as executing these four A's acrossa diverse and large mix of systems is the source of inefficiency, and ultimately security vulnerabilities, this same diversity (or complexity) makes approaching governance on an ad-hoc basis inadvisable. What do you start with, and what do you leave out? There are simply too many ingredients required to make the soup, and too many cooks in the kitchen.
Governance for the vast majority of organizations looks like this:
- Many and varied systems (applications, data sources, capabilities, etc.) that users must access to do their jobs both on-prem and in the cloud
- Too many different ways that access is granted
- Many different IT teams with too narrow an area of expertise
- Too little knowledge from the business of how these things work
- Too little knowledge from IT as to why they need to work in a certain way, and what the implications are if they don't
- Too much reliance on 'this is the way we've always done it'
- Too much blind verification … 'If Joe has the same access as Sally, it must be right…right?'
- Too much security policy developed by those that implement it (IT) rather than those on the hook if it goes wrong (the business)
- Too little visibility by the business into what access people have and how they got it
- Too little attention to finding areas of risk and remediating them
An approach to access governance that gets it right includes prerequisites to governance like good provisioning, strong policy, adequate visibility, and a complete understanding of who can access what. All this would be tightly coupled with the ability for the right people to easily have access to the information they need to do precisely that – govern. Only the One Identity family of IAM solutions and One Identity Manager in particular provides these governance-enabling capabilities without the heavy overhead of a cumbersome and rigid framework, or the myopic inadequacy of a focus only on one area, one type of user, or one aspect of governance.
Too many closed loops
Many organizations take a stance that governance begins and ends with user access to applications. It's understandable since applications are highly visible. Applications are most easily understood and have been targets for governance initiatives and vendor solutions for many years. And applications absolutely must be governed. But how many applications do you have and how many 'closed loops' do you end up with? How many manual processes exist that put the IT team and line-of-business personnel on different pages? How difficult is it to provide even the most basic governance information?
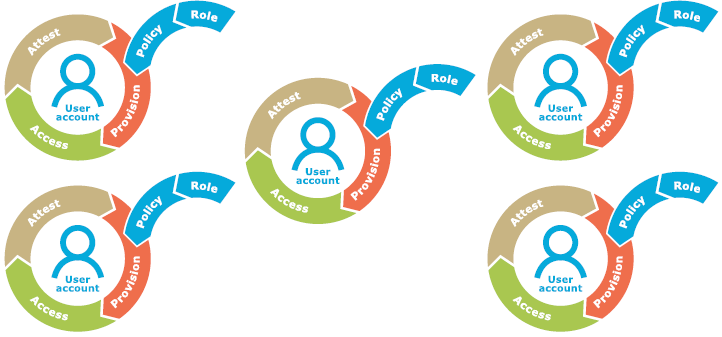
Figure 2. Traditional approaches to governance implement separate closed loops for each system or scenario that must be governed
Governance done right would provide a unified governance approach for all applications, which can move you miles closer to agility. Ideally, you want them to be tied to an equally unified enterprise provisioning approach with a single source of the truth for policy, workflow, roles and approvals.
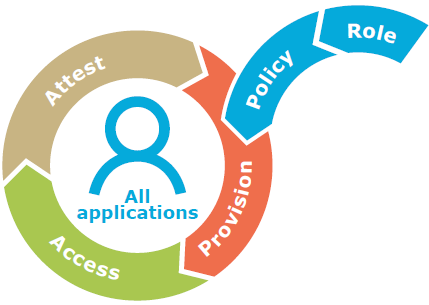
Figure 3. A unified approach to governance provides a single closed loop that encompasses all access needs.
But applications are only part of the story. A very large percentage of data at any organization can be classified as unstructured.
Unstructured data exists outside of the strictly organized confines of a database. Unstructured data can be spreadsheets, PDFs, videos, audio files, PowerPoint presentations or Word documents.
These can contain benign information that's not governance demanding, but very often they contain critical data regulated by compliance. For example, spreadsheets that contain personally identifiable information such as Social Security numbers, birthdates and addresses must be governed. Proprietary information, such as trade-secrets, plans and financial performance, often exists in PDFs and PowerPoint presentations. Unfortunately, unstructured data exists in myriad places – many outside of the control of IT. File shares, NAS devices, cloud storage services, and SharePoint sites may contain sensitive unstructured data. In many cases, the best an organization can do to govern these resources is to roughly control access to the server or file share itself – a lowest common denominator approach that either is too restrictive for efficiency, or too lenient for compliance.
So governance of access to unstructured data often follows the same path as application access governance: disjointed, nonexistent, manual or inconsistent. Bottom line, doing the best you can with what you have is not good enough. Our closed loop governance model reflects the challenges of provisioning, providing appropriate access and attestation. These challenges are magnified as the diversity of locations for unstructured data expand and more of those locations slip out of the control of IT – the ever-popular SharePoint gone wild! In some areas closed loops exist. In others they don't.
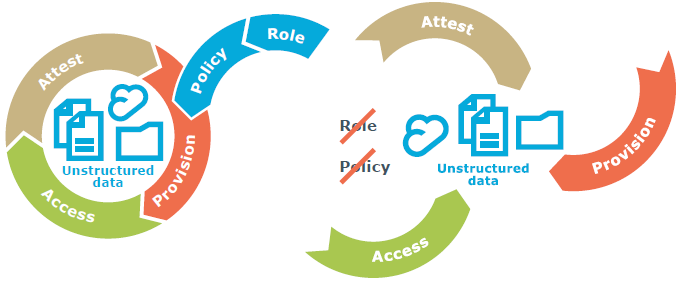
Figure 4. It is difficult to implement a closed loop governance model on disparate sets and locations of unstructured data.
The number of circles representing governance of unstructured data could be much larger than those representing application access. And the potential for rogue cloud storage locations, non-governed access permissions and sensitive data being innocently put at risk is extremely high.
If you're looking to do it right, it makes no sense to address governance of unstructured data independently of application access. The users are the same, the roles that should control access should be identical, and the line-of-business personnel that are on the hook to attest to access don't change when the app or data being accessed is different or more difficult to govern.
Privileged accounts—such as the UNIX root account, an application administrator account, or the superuser account required to administer any system—are a governance nightmare. Their high level of access rights, their anonymous nature and the lack of visibility makes them high risk.
If governance of unstructured data is difficult, then governance of privileged access (discussed in the next section of this book) is nearly impossible when approached in the disjointed manner so often applied to shared superuser access. Application access has matured to the point that, if you want governance, you can get it. Data governance is in a similar state, though less visible. However, the vast majority of privileged account activities are mired at the access and security levels of the hierarchy, barely dipping their toes in control or management. Governance for privileged access struggles to achieve a closed-loop model.
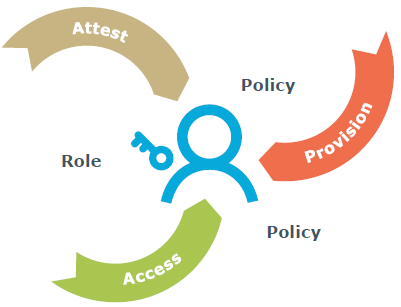
Figure 5: Governance for privileged access typically struggles to achieve a closed-loop model.
Governance for privileged access is often the realm of 'we have controls in place, but we can't prove that they are working.' Many organizations are able to control the issuing and use of superuser credentials, and some are even able to watch what is done with those rights. Yet true governance activities of provisioning, attestation, and reporting are done manually in silos by the very people they are meant to govern at best. At worst, they are ignored altogether.
But administrators are people too. They have roles. They have identities in systems. They have policies that are meant to control what they do. And they have supervisors that are required to attest to their access rights. Auditors don't give you a pass just because those accounts are more difficult to govern, or you don't have the tools to make what you have to do any easier.
A real-world approach to privileged access governance unifies those things that control access, such as roles, identities and policies. It accomplishes this with tools that enable the line-of-business to understand, control and attest to appropriate administrator access across the entire range of systems.
A unified approach to identity governance that does it right would be able to govern user access to applications, user access to unstructured data and administrator access to systems. It would look like this:
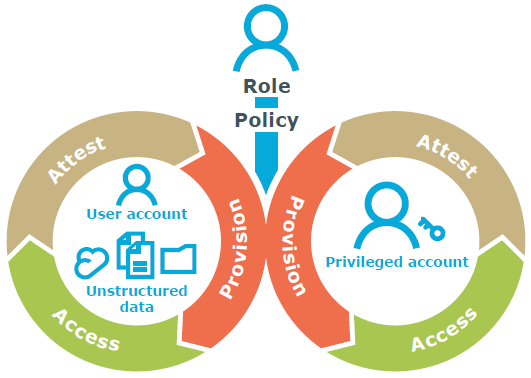
Figure 6. The right approach to governance would encompass application access, data access, and privileged access in a unified manner.
A few important action points can be learned from viewing governance in a holistic way:
- Move as much of the control, decision making and visibility required for governance away from IT and onto the business to solve many problems
- Reduce the number and disparity of points of audit to increase accuracy and accelerate compliance
- Avoid blind verification
- Involve the business in the development and execution of policy – IT knows how to do things, but isn't paid to know why they are done
- Integrate provisioning, access request, recertification/attestation and compliance reporting as tightly as possible
- Implement analytics to identify and mitigate areas of risk and misaligned ownership and responsibility within those governed systems and access scenarios
- Remember the entire range of access when dealing with governance – it's about identities and accounts, applications and data for both general users and privileged users
Identity governance done right takes into account the complexity of organizations, the merciless nature of compliance, the heavy workload of both IT and line-of-business personnel, and the understanding that governance is an ongoing journey and not a final destination. The right solution for identity governance will empower the business to own governance. This capability is sorely missing in most legacy IAM framework solutions.
An international oil and gas exploration company had big challenges when it came to access governance. The company's requirement to share information with partners was proving difficult to achieve without placing sensitive information at risk. Efforts to restrict access through traditional IAM framework technology were a managerial nightmare, due to the constantly evolving population of internal and third parties that needed access. However, opening access up was not an option due to the proprietary nature of the data. Adding to this challenge was the fact that much of the required information sharing was taking place in a rogue fashion with no corporate oversight and a high amount of risk. When it came time to satisfy the strict regulatory requirements of the energy industry, simply providing accurate data on information exchange and access rights was near impossible.
The company solved its problems by standardizing its access governance processes on a single foundation of uniform processes, unified policy, complete visibility and a high-amount of 'self-service.' Internal employees and third parties could request access as they needed it and be automatically granted appropriate access when policy requirements were satisfied.
This real-world approach to access governance, gave this company a single source of the truth for access request, fulfillment (provisioning), recertification and attestation, and compliance for application and unstructured data access. In addition, IT was relieved of a majority of the tedious and error-prone processes that were once so fundamental to access management.
One Identity has been used by thousands of companies to address their IAM needs, including a quickly growing roster of organizations using One Identity for business-centered access governance and privileged account governance. One Identity unites access management, privileged account management and identity governance through a single, business-centric, future-ready foundation. It ensures that governance is done right – affordably and securely. This proven solution places control in the hands of the business with the visibility needed to ensure security and compliance balanced with trouble-free access to applications and data.
Among the identity governance capabilities available through One Identity, some of the most prominent include:
- Enterprise provisioning
- Access request and certification
- Governance of unstructured data
- Role engineering
- Privileged account governance
- The ability to rapidly and completely embrace cloud assets in a provisioning and governance implementation
- Identity analytics to identify and remediate instances of permissions and entitlements that are out of line with norms, policy, and best practices